12 Types of Phishing Attacks and How to Identify Them
Cyber Security Awareness: What Are Phishing Attacks?
Phishing attacks are the practice of malicious actors sending fraudulent communications that appear to come from a legitimate trusted source.

At its core, phishing is an attack methodology that uses social engineering tactics to make a person take an action that is against their best interests.
The goal of the attack is to steal victims sensitive data like credit cards and login information or to install malware on the victim’s device.
Phishing is one of the most common types of cyberattacks so, it’s apparent that everyone learn about them in order to protect themselves and their organizations.
Results Of Phishing Attacks
A phishing attack can cause devastating results.
For individuals, this includes unauthorized purchases, stealing funds, or identify theft.
For organizations, this includes severe financial losses in addition to declining market share, reputation, and consumer trust.
Depending on the scope of the attack, phishing could escalate into a security incident from which a business will have a very tough time recovering from.
With a better understanding of the twelve types of phishing attacks and how to identify them, individuals and organizations can better protect themselves.
12 Types Of Phishing Attacks:
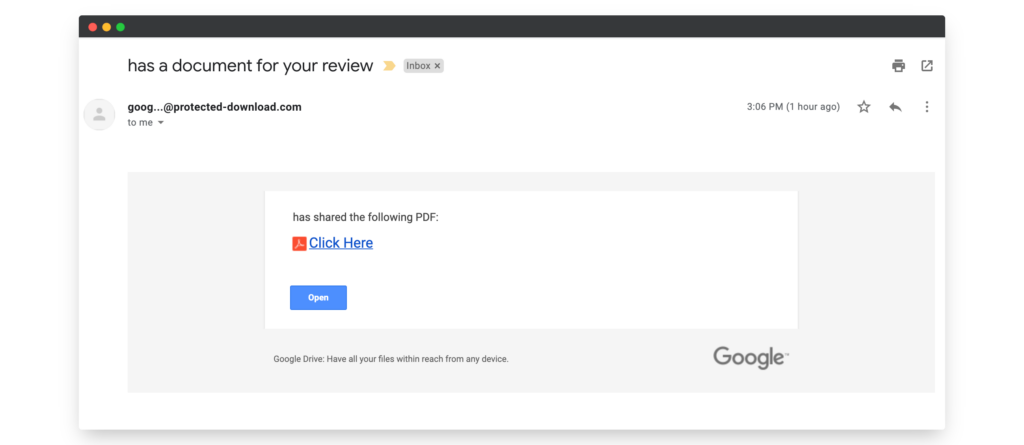
1. Email Phishing
Email phishing, also called “deception phishing,” is one of the most well-known attack types.
Malicious actors send emails to users impersonating a known brand, and create a heightened sense of urgency to act, then lead people to click on a link or download an asset.
The links traditionally go to malicious websites that either steal credentials or install malicious code, known as malware, on a user’s device.
The downloads, usually PDFs, have malicious content stored in them that installs the malware once the user opens the document.
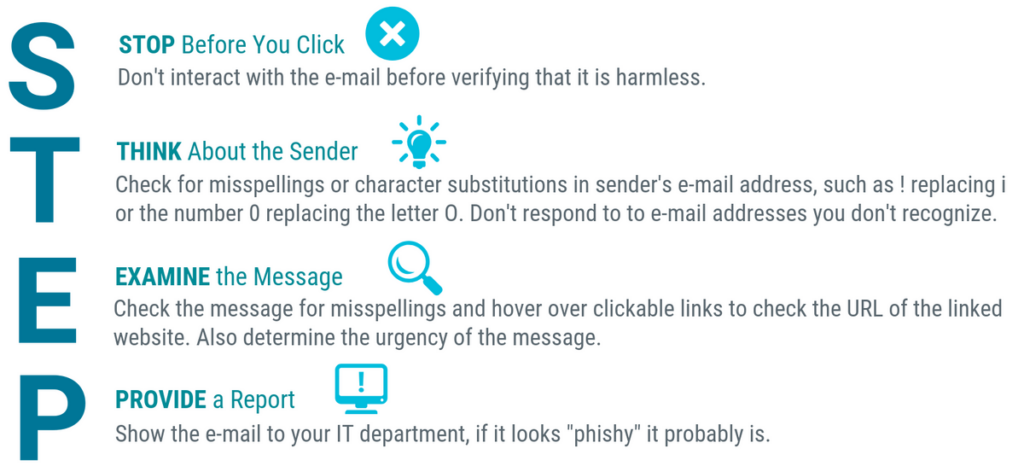
How To Identify Email Phishing:
- Legitimate information: Look for contact information or other legitimate information about the organization being spoofed, then look to identify things like misspellings or a sender email address that has the wrong domain.
- Malicious and benign code: Be aware of anything including code that tries to trick Exchange Online Protection (EOP) such as downloads or links that have misspellings.
- Shortened links: Do not click on any shortened links because these are used to fool Secure Email Gateways.
- Fake brand logo: Review the message for any logos that look real because they may contain fake, malicious HTML attributes.
- Little text: Ignore emails that have only an image and very little text because the image might be hiding malicious code.
2. HTTPS Phishing
The hypertext transfer protocol secure (HTTPS) is often considered a “safe” link to click because it uses encryption to increase security.
Most legitimate organizations now use HTTPS instead of HTTP because it establishes legitimacy. However, cybercriminals are now leveraging HTTPS in the links that they put into phishing emails.
How to identify HTTPS Phishing link:
- Shortened link: Make sure that the link is in its original, long-tail format and shows all parts of the URL.
- Hypertext: These are “clickable” links embedded into the text to hide the real URL.
3. Spear Phishing
Although spear phishing uses email, it takes a more targeted approach. Cybercriminals start by using open source intelligence (OSINT) to gather information from published or publicly available sources like social media or a company’s website.
Then, they target specific individuals within the organization using real names, job functions, or work telephone numbers to make the recipient think the email is from someone else inside the organization.
Ultimately, because the recipient believes this is an internal request, the person takes the action mentioned in the email.
How to identify Spear Phishing:
- Abnormal request: Look out for internal requests that come from people in other departments or seem out of the ordinary considering job function.
- Shared drive links: Be wary of links to documents stored on shared drives like Google Suite, O365, and Dropbox because these can redirect to a fake, malicious website.
- Password-protected documents: Any documents that require a user login ID and password may be an attempt to steal credentials.
4. Vishing
Voice phishing, or “vishing,” happens when a cybercriminal calls a phone number and creates a heightened sense of urgency that makes a person take an action against their best interests.
These calls normally occur around stressful times. For example, many people receive fake phone calls from people purporting to be the Internal Revenue Service (IRS) during tax season, indicating that they want to do an audit and need a social security number.
Since the call creates a sense of panic and urgency, the recipient can be tricked into giving away personal information.
How to identify Vishing:
- Caller number: The number might be from an unusual location or blocked.
- Timing: The call’s timing coincides with a season or event that causes stress.
- Requested action: The call requests personal information that seems unusual for the type of caller.
5. Smishing
Malicious actors often apply similar tactics to different types of technologies. Smishing is sending texts that request a person take an action.
These are the next evolution of vishing. Often, the text will include a link that, when clicked, installs malware on the user’s device.
How to identify Smishing:
- Delivery status change: A text requesting that the recipient take action to change a delivery will include a link so always look for emails or go directly to the delivery service website to check status.
- Abnormal area code: Review the area code and compare it to your contacts list before responding to a text or taking a suggested action.
6. Content Spoofing / Pharming:
Pharming is more technical and often more difficult to detect. The malicious actors hijack a Domain Name Server (DNS), the server that translates URLs from natural language into IP addresses.
Then, when a user types in the website address, the DNS server redirects the user to a malicious website’s IP address that might look real.
How to identify Pharming:
- Insecure website: Look for a website that is HTTP, not HTTPS.
- Website inconsistencies: Be aware of any inconsistencies that indicate a fake website, including mismatched colors, misspellings, or strange fonts.
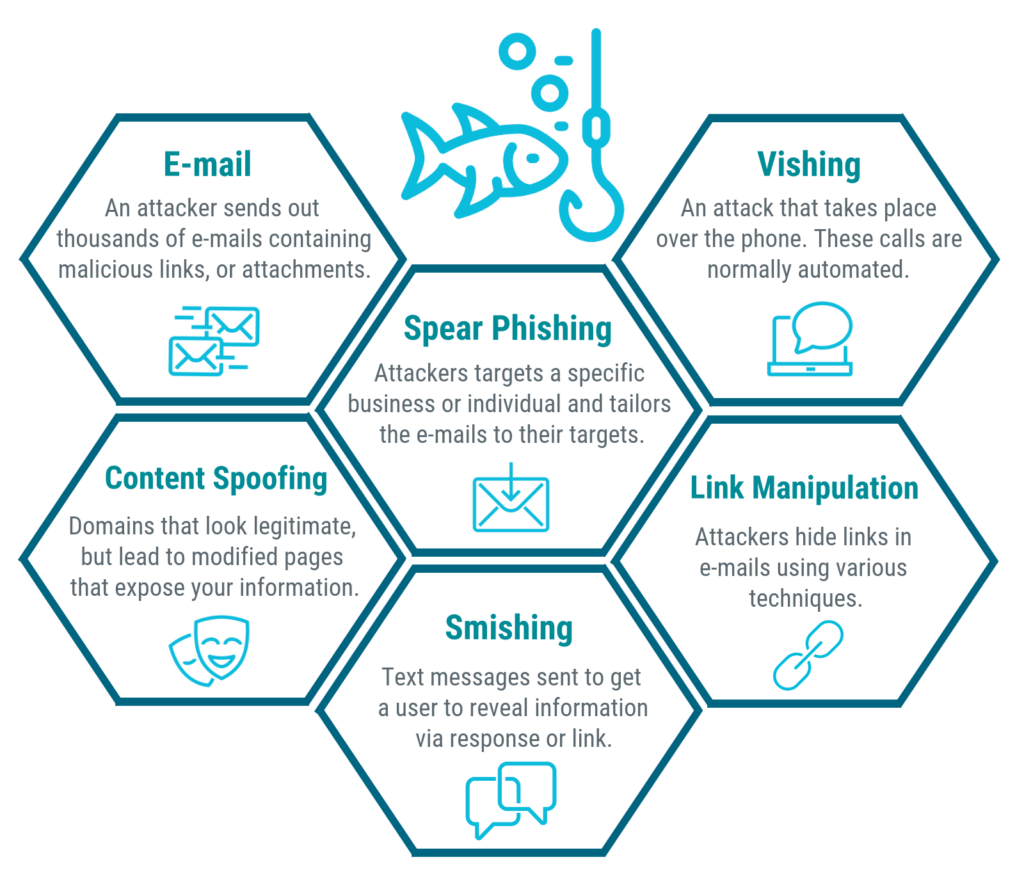
7. Angler Phishing
As malicious actors move between attack vectors, social media has become another popular location for phishing attacks.
Similar to both vishing and smishing, angler phishing is when a cybercriminal uses notifications or direct messaging features in a social media application to entice someone into taking action.
How to identify Angler Phishing:
- Notifications: Be wary of notifications that indicate being added to a post because these can include links that drive recipients to malicious websites.
- Abnormal direct messages: Be on the lookout for direct messages from people who rarely use the feature since the account might be spoofed, or fraudulently recreated.
- Links to websites: Never click a link in a direct message, even if it looks legitimate, unless the sender regularly shares interesting links this way.
8. Whaling/CEO Fraud
Another type of corporate phishing that leverages OSINT is whale phishing, also called whaling or CEO fraud.
Malicious actors use social media or the corporate website to find the name of the organization’s CEO or another senior leadership member.
They then impersonate that person using a similar email address. The email might ask for a money transfer or request that the recipient review a document.
How to identify CEO Fraud:
- Abnormal request: If a senior leadership member has never made contact before, be wary of taking the requested action.
- Recipient email: Since many people use email applications that connect all their email addresses, make sure that any request that appears normal is sent to a work email not personal.
9. Pop-Up Phishing
Although most people use pop-up blockers, pop-up phishing is still a risk.
Malicious actors can place malicious code in the small notification boxes, called pop-ups, that show up when people go to websites.
The newer version of pop-up phishing uses the web browser’s “notifications” feature. For example, when a person visits a website, the browser prompts the person with “www._____.com wants to show notifications.” When the user clicks “Allow,” the pop-up installs malicious code.
How to identify Pop-Up Phishing:
- Irregularities: Review for spelling errors or abnormal color schemes.
- Shift to full-screen mode: Malicious pop-ups can turn a browser to full-screen mode so any automatic change in screen size might be an indicator.
10. Clone Phishing
This targeted attack leverages services that someone has previously used to trigger the adverse action. Malicious actors know most of the business applications that require people to click links as part of their daily activities.
They will often engage in research to see what types of services an organization uses regularly then send targeted emails that appear to come from these services.
For example, many organizations use DocuSign to send and receive electronic contracts, so malicious actors might create fake emails for this service.
How to identify Clone Phishing:
- Abnormal timing: Be wary of any unexpected email from a service provider, even one that is part of normal daily job function.
- Personal information: Look out for emails requesting personal information that the service provider never asks for.
11. Evil Twin Phishing
An evil twin phishing attack uses a fake WiFi hotspot, often making it look legitimate, that might intercept data during transfer.
If someone uses the fake hotspot, the malicious actors can engage in man-in-the-middle or eavesdropping attacks. This allows them to collect data like login credentials or sensitive information transferred across the connection.
How to identify an Evil Twin Phishing:
- “Unsecure”: Be wary of any hotspot that triggers an “unsecure” warning on a device even if it looks familiar.
- Requires login: Any hotspot that normally does not require a login credential but suddenly prompts for one is suspicious.
12. Watering Hole Phishing
This starts with malicious actors doing research around the websites a company’s employees visit often, then infecting the IP address with malicious code or downloads.
These can be websites that provide industry news or third-party vendors’ websites. When the user visits the website, they download the malicious code.
How to identify Watering Hole Phishing:
- Pay attention to browser alerts: If a browser indicates that a site might have malicious code, do not continue through to the website, even if it’s one normally used.
- Monitor firewall rules: Ensure that firewall rules are continuously updated and monitored to prevent inbound traffic from a compromised website.
How To Report Phishing
Reporting attack attempts helps others stay safe from similar threats in the future!
- Phishing Email: Forward it to the Anti-Phishing Working Group at reportphishing@apwg.org
- Phishing Text: forward it to SPAM (7726).
- Report the phishing attempt to the FTC at ReportFraud.ftc.gov.
Phishing Awareness Training For Your End Users
It’s 2023 and Cyber Crime is still on the rise. Cyber criminals continue to relentlessly attack organizations, big and small, with more sophisticated emails, phishing, and social engineering tactics.
- 89% of phishing attacks orchestrated by professional cyber crime organizations.
- 66% of malware is now installed via malicious email attachments and advanced spear phishing techniques, costing business on average $140,000.
- 41% of IT Pros report AT LEAST DAILY phishing attacks.
- 30% of phishing emails are opened.
It’s essential that your business stay ahead of the curve, implementing a multi-layer security posture with physical controls, software controls, and end user training to prevent your easiest target from falling victim.
Here at BVA Technology Services we are partnered with Sophos to keep businesses and users safe and up to date. We highly recommend Sophos Phish Threat Service, it provides effective phishing simulations, automated training, and comprehensive reporting.
Sophos Phish Threat is a phishing attack simulation and training for your end users!
For just ($2.90/month) we’ll set you up with Sophos Phish Threat, so your organization can begin cultivating a positive security awareness culture through testing, training, and reporting.
How Phish Threat Works:
- On a reoccuring basis, Phish Threat sends out 1 of 500 realistic phishing attacks to your internal staff.
- Each email is tracked to see who opens the email, clicks on any links, and/or provides their credentials.
- Any users caught are automatically enrolled in an interactive training module that will educate the end user about the specific threat in that particular email.
- Users can report the suspected phishing email wtih the user of an outlook add-in.
- All actions are gathered in Sophos Central to provide comprehensive reporting on the users who have been caught, the number of times they have been caught, and if they have completed the training or not. This allows you to enforce accountability of those trainings.
What The Phishing User Training Covers:
- Current phishing, credential harvesting, and malicious attachment campaigns.
- Socially relevant attack simulation templates.
- Scheduled Monthly Training Campaigns.
- Covering multiple scenarios from beginner to expert.
While there’s no silver bullet when it comes to preventing all cyber security attacks, putting appropriate measures and training in place can significantly reduce the chances of it happening.








