Think Your Datas Been Breached? What To Do Next
Have you been involved in a data breach? Find out if your data’s been breached and what to do if it is.

This guide will help you find out where and when, and lists the steps you should take next.
Data breaches are security incidents we now hear about in every day cybersecurity news. They strike every industry, every sector, every county.
Technology is only becoming more complex and sophisticated, which unfortunately means so are the cyber threats we’re being faced with. Victims can be everything from small, independent businesses to Fortune 500 companies.
Every organization needs to be prepared with both cyber liability insurance and an effective cyber security plan to manage and mitigate cyber risk. Being without it means it’s not a question of if your organization will suffer a breach, but when.
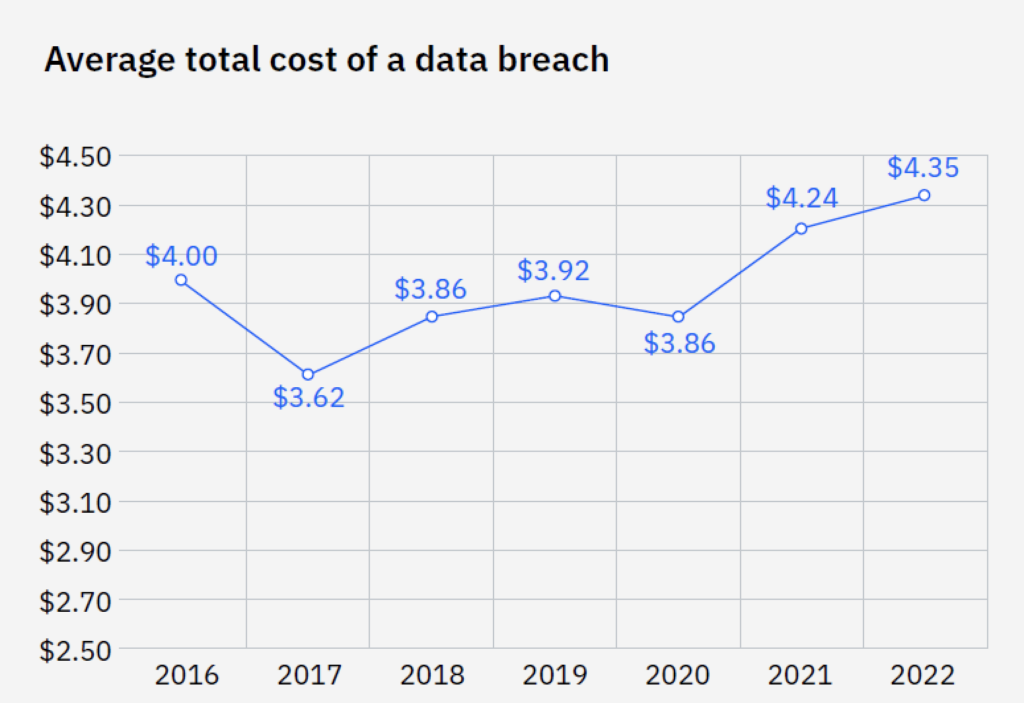
IBM estimates that the average cost of a data breach in 2021 for US companies was $4.24 million, and damages increased by an average of $1.07 million when remote working was involved.
However, talk of the millions of dollars corporations spend to repair damaged systems, perform cyber forensics, improve their cyber defenses, and cover legal fees, doesn’t necessarily convey all the costs felt by individual customers involved in a data breach.
For individuals, the costs can be more personal, because while financial damage may be a factor, the loss may be in the form of salaries, savings, and funds in investments.
Here’sa guide highlighting how data breaches occur, how they can impact you,the tools you can use to determine if your account is at risk, and what you can do in the aftermath.
How Do Data Breaches Happen?
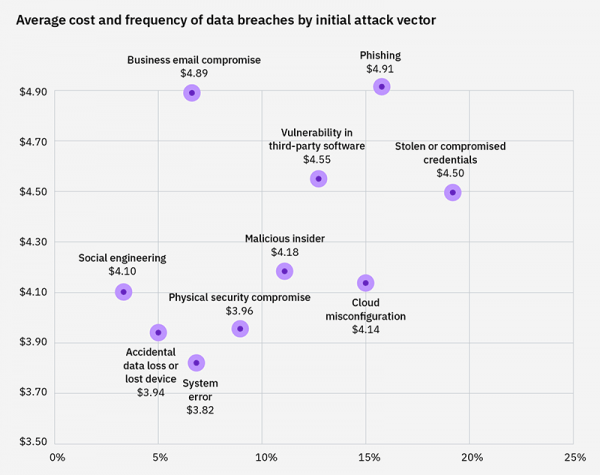
According to IBM, the most common initial attack vector cyberattackers use to break into a company’s network is the use of compromised credentials, an approach that is responsible for 20% of breaches.
These credentials can include account usernames and passwords leaked online, stolen in a separate security incident, or obtained through brute-force attacks, in which automatic scripts try out different combinations to crack easy-to-guess passwords.
Other Potential Cyber Attack Methods:
Magecart Attacks: Malicious code is quietly injected into e-commerce payment pages to harvest your payment card information.
Malicious Code (injected into website domains and forms): The same tactics can be used to grab other forms of data from customers and visitors, with data stolen directly from unaware victims visiting a legitimate service.
Business Email Compromise (BEC) scams: BEC scams occur when an attacker pretends to be a company employee, contractor, or service provider. They latch on to email threads or contact a staff member, such as one working in the payments or customer service departments, to trick them into handing over information or paying an invoice to the wrong bank account.
Insider Threats: Sometimes employees have personal problems with their company, or they’re made an offer by cybercriminals that they don’t refuse. This can lead to your information changing hands, or an inside source installing malware on their employer’s network.
Negligence: Unsecured servers, left open and exposed online likely due to misconfigurations, are a principal reason for data exposure and breaches. Information may also be leaked accidentally by employees.
Phishing Attacks: Cybercriminals will sending fraudulent communications that appear to come from a legitimate trusted source. The goal of the attack is to steal victims sensitive data like credit cards and login information or to install malware on the device.
What Happens When Attackers Are Inside?
The attacker may conduct surveillance first, mapping a network to work out where the most valuable resources are or to discover potential pathways to jump into other systems.
Verizon says that 71% of data-related incidents are financially motivated. Attackers may deploy ransomware to blackmail their victims into paying up to regain their access to the network.
In so-called “double-extortion” tactics, hacking groups may first steal confidential information and then threaten to leak it online.
Alternatively, some may grab and go, stealing the intellectual property they came for and then erasing their tracks. Others may test their access point and sell it to other cyber attackers via the dark web.
In some cases, network intrusions are for one reason alone: to disrupt services and damage a company.
Some miscreants download data and make these data dumps freely available online, posting them to resources such as PasteBin.
How Do Data Breaches Impact You?
If you’ve been involved in a data breach as a user or customer, your records may have also been exposed, stolen, or leaked online, as in the cases below:
- Securitas: In January, researchers disclosed unsecured AWS buckets belonging to the security company, left exposed online. Airport employee records and PII were leaked.
- Shanghai National Police (SHGA) database: In July, reports suggested that data collected by SHGA, impacting approximately 1 billion Chinese citizens, was spotted for sale on the Dark Web.
- Robinhood: A 2021 security incident resulted in the personal information and email addresses of roughly 5 million people being stolen.
- Facebook: A data dump including information belonging to 553 million Facebook users was released online in 2021, two years after being harvested.
- Volkswagen, Audi: Last year, the companies admitted to a data breach impacting 3.3 million customers and interested buyers.
Your personally identifiable information (PII), including your name, physical address, email address, work history, telephone number, gender, and copies of documents including passports and driving licenses, can all be used to conduct identity theft.
ID theft is when someone uses your information without permission to pretend to be you. They may use your identity or financial data to conduct fraud and commit crimes.
This can include tax-related fraud, opening up lines of credit and loans in your name, medical fraud, and making fraudulent purchases online.
As cybercrime is global, it can also be extremely difficult for law enforcement to prosecute the perpetrators.
Criminals may also ring up a company you use, such as a telecoms provider, and pretend to be you to dupe customer representatives into revealing information or making changes to a service, such as in the case of SIM-swapping attacks.
These scenarios can impact your credit score, make you financially responsible for a loan or payment you didn’t agree to, and lead to serious stress and anxiety in cleaning up your name and finances.
Blackmail can also be a factor. When extramarital affairs website Some victims were contacted by cybercriminals threatening to tell their partners, friends, and colleagues about their activities unless they were paid.
How To Know If Your Data Has Been Breached
Typically, your service provider will contact you through email or letters, explaining that your information has been compromised. However, companies may take weeks or months to contact you, if at all.
Therefore, it is also up to you to keep an eye on the news for any recently disclosed data breaches, and there are also handy tech tools available that you can take advantage of:
Have I Been Pwned
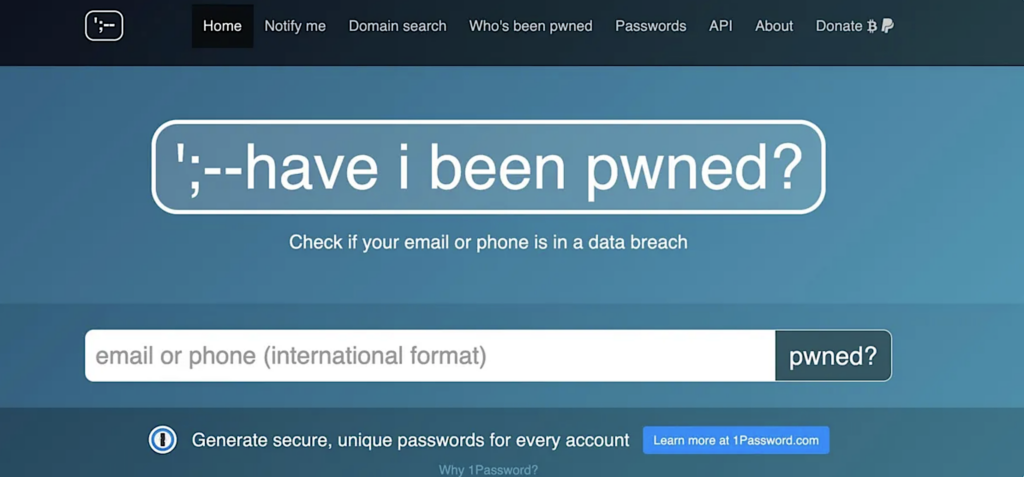
Have I Been Pwned, operated by security expert Troy Hunt, it’s the first resource you should use to find out what data breaches you have been involved in and how extensively your data has been leaked.
The search engine allows you to search either by your email address or phone number.
The site will flag any breaches containing your data, and when they happen, by cross-checking billions of leaked records that have been added to the Have I Been Pwned database.
If you type in your details and are rewarded with a green screen, congratulations, you haven’t been involved in any notable data security incidents!
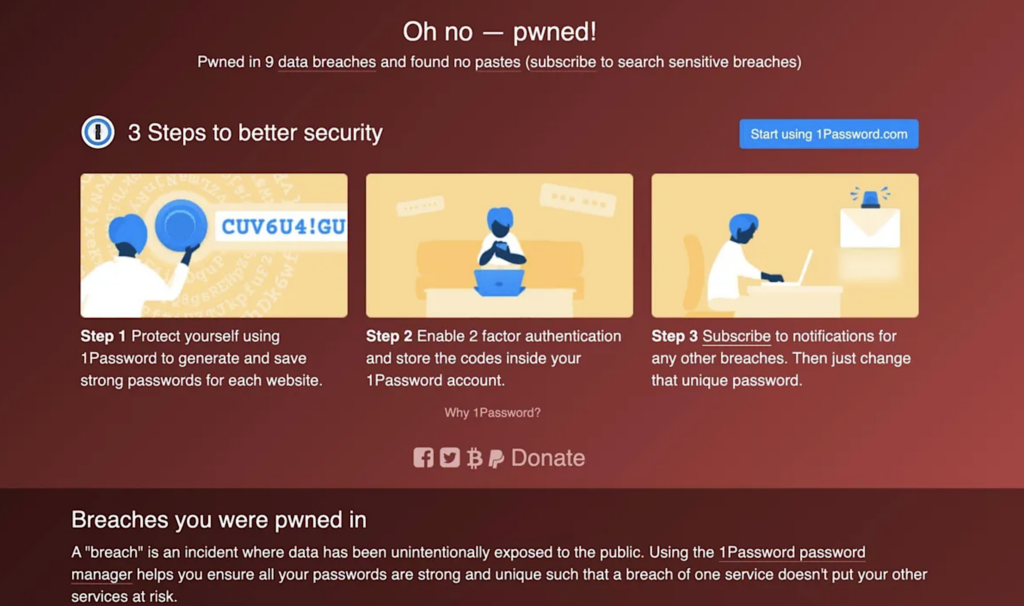
However, if you have, you will see a screen (shown below) telling you which breaches have impacted you.
What To Do If You’ve Been Breached
What you do next depends on the severity and type of data breach.
The likelihood is that you have already had your PII leaked in some form or another online regarding basic details, such as your name and email address. In this scenario, there is not much you can do.
However, if your online account details have been compromised, whether or not the password is hashed, you should change it immediately.
In addition, if you are guilty (as many of us are) of reusing password combinations across different platforms and services, you should also change them ASAP.
If you use a password locker or manager, these platforms will usually warn you if the same passwords are being used across multiple services.
Whenever you can, enable two-factor authentication (2FA), also known as multi-factor authentication (MFA), which implements a second layer of security on your accounts, so if your credentials have been leaked, attackers would also need access to your email account or handset to grab the verification code required to access your account.
It would help to consider using a physical YubiKey security key for any central “hub” accounts, such as your Gmail or Microsoft email address.
If an attacker manages to steal the credentials for these accounts, this can grant them the keys to your entire digital kingdom. Without access to the physical key, attackers are stopped in their tracks.
Whether or not financial information is involved, if enough personal data is available online, ID theft and fraud are still a risk.
Unfortunately, credit monitoring services are now necessary to be alerted to suspicious activity that could place your reputation, finances, and creditworthiness at risk.
However, even if you aren’t willing to pay for a premium subscription, you should still consider signing up for a free option.
If your payment card details, bank accounts, or other digital financial services have been compromised, call the provider immediately (or if you have a mobile app with the feature, freeze your cards).
You must also inform your bank or financial services provider so they can be on the lookout for suspicious and fraudulent transactions.
In this world, data is cheap and unnecessarily collected in bulk by companies that don’t protect it effectively or govern themselves in data collection practices well.
When a breach occurs, you are most often just offered a year or so of free credit monitoring.
Credit Monitoring Services: Including Experian and LifeLock, are beginning to integrate data breach monitoring, too, as these situations can result in identity theft.
A criminal act can severely impact your credit reports and scores. However, unless you have notifications enabled, you may not be warned of any changes unless you have logged in.
Unfortunately, it is up to individuals to deal with the fallout, and knowing you’ve been involved in a data breach is half the battle.
Protecting yourself by maintaining adequate account security, changing your passwords frequently, and being on the alert for suspicious activities are ways you can mitigate the damage these frequent security incidents can cause.








