What Does The Dark Web Mean For Cyber Security
The dark web, or darknet, is the part of the internet that is difficult to access without the proper tools and authorizations.

An average, everyday web surfer using a commonly-available web browser like Chrome or Explorer isn’t likely to be taking a virtual walk on the dark side, but security leaders still must make an effort to understand the cyber threats the darknet pose.
While the darknet has some legitimate purposes, it is often used by cybercriminals to organize and execute ransomware and DDoS attacks and to sell information stolen from companies and individuals.
The dark web is a part of the internet that is only accessible with a special browser. It has legitimate uses, but abuse by malicious actors is a cybersecurity problem.
A web search for “dark web” and “ransomware” turns up a wealth of news about ransomware gangs selling and threatening to sell stolen information.
To manage cybersecurity risks, it’s important to be aware of dark web threats and stolen information.
What Is The Dark Web?
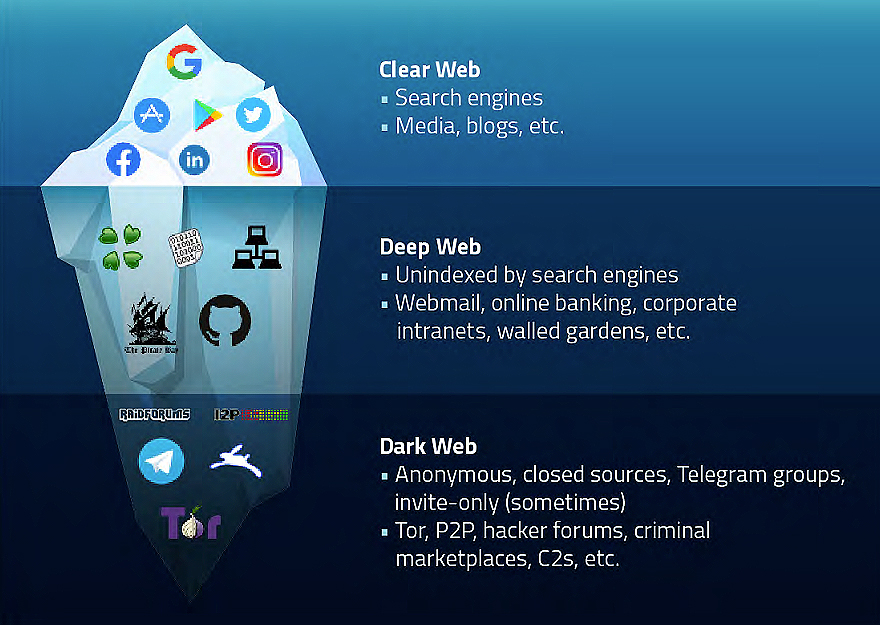
The internet as a system can be divided into three layers: the clear, the deep, and the dark web.
The Clear Web: The internet most of us use on a daily basis.
Millions of websites and pages are indexed by search engines, and you can access them from a typical browser, such as Safari, Chrome, or Firefox.
It is a substantial, but small, fraction of the web (5-10%). No passwords are needed to connect to the surface web; you just search and browse.
The Deep Web: The layer underneath, search engines cannot index it, and it requires a specific browser authentication to access.
Most people use parts of the deep web every day for accessing things like web mail, pay-walled news articles, non-public social media profiles and posts, etc.
Deep web content also includes things like medical records, government records, missing persons information, and organization’s website areas that are for internal use only.
The Dark Web: A small subset (4-5%) of the deep web. It is only accessible through a special browser, and is an area that is associated with criminal activity.
This can include the sale of information, illegal products, drugs, weapons, and other illicit material. The Onion Router browser is the most well-known dark web browser, and is best known for the anonymity it offers its users.
However, the dark web also includes other overlay networks that can only be accessed with specific software/configurations. These include peer-to-peer networks and anonymity networks like I2P, Freenet, Retroshare, GNUnet, Syndie, OneSwarm and Tribler.
Why Was The Dark Web Created?
The Onion Router and the dark web began in the 1990s as US government research funded by the US Naval Research Laboratory, and later by the Defense Advanced Research Projects Agency (DARPA).
The goal was an anonymous information exchange across the internet.
In 2004, The Onion Router code was released under a free license, and in 2006 the not-for-profit TOR Project was created.
Dissidents, activists, journalists began to use TOR to communicate while protecting identities. However, criminals also began using it and the dark web for illegal activities.
What Does The Dark Web Mean For Cyber Security?
Monitoring the dark web for information that can be used to target your business helps get ahead of threats.
Stolen login credentials are of particular concern, representing 37% of data breaches. Illegal dark web forums and marketplaces sell stolen credentials, other stolen information, and malware.
Malicious actors use the stolen information to target businesses to gain network access for ransomware attacks and more.
- Phishing emails can use stolen business information to appear more authentic. Unwitting victims can be tricked into revealing login credentials, or into allowing malware directly onto networks.
- Credential stuffing attacks use stolen login credentials in bulk to take advantage of password reuse and infrequent password updates. The attacks try to find a match in your business network to gain unauthorized access.
How Can You Protect Against Dark Web Cyber Threats?
Use a good dark web monitoring service to detect and anticipate cybersecurity threats to your business. These services infiltrate hubs of cybercriminal activity like illegal marketplaces and forums for cybercriminals.
They monitor for stolen data and other information on organizations or employees.
They also monitor dump sites like Pastebin, where anonymous people can post information including stolen confidential documents, emails, databases and other sensitive data.
Cyber security awareness matters for everyone, even people who don’t think they use technology directly.
Nearly every aspect of modern life involves sharing digital information, make sure yours is secure.








