If you haven’t updated your firewall in the last few years, chances are you’re putting your business at risk. In today’s computing environments, firewalls block certain data from transitioning from one part of a network to another. This is particularly important when it comes to isolating the internet from a local area network, since traffic […]
Cybercriminals have been targeting more and more Mac users recently and by taking the proper actions, you can fully safeguard your Mac against attacks. Cybersecurity doesn’t have to be complicated, you can easily protect your Mac and your most sensitive data in a few simple steps. Macs do have built-in security settings, but they’re often not used effectively leaving your […]
Microsoft brings users a great operating system for personal computers, and while it has built-in security features they are not enough to fully protect yourself. Therefore, you need to improve the security level of your computer, which will make it more secure against viruses, malware, other malicious programs and even hackers. Here are the top […]
Microsoft has started making its next release of Windows Server, known as Windows Server 2022, available to mainstream users on the Volume Licensing Service Center. Windows Server 2022, which Microsoft has been developing for the past year-plus, is a Long Term Servicing Channel (LTSC) release and includes several new features. Windows Server 2022 comes in Standard, […]
Exploiting security flaws is one of the major tactics used by cybercriminals to attack organizations. Vulnerabilities are an unfortunate fact of life for operating systems, applications, hardware devices and databases. An attack against a database can easily compromise sensitive and confidential user and customer data. Based on analysis fromImperva covering 27,000 on-premises databases around the […]
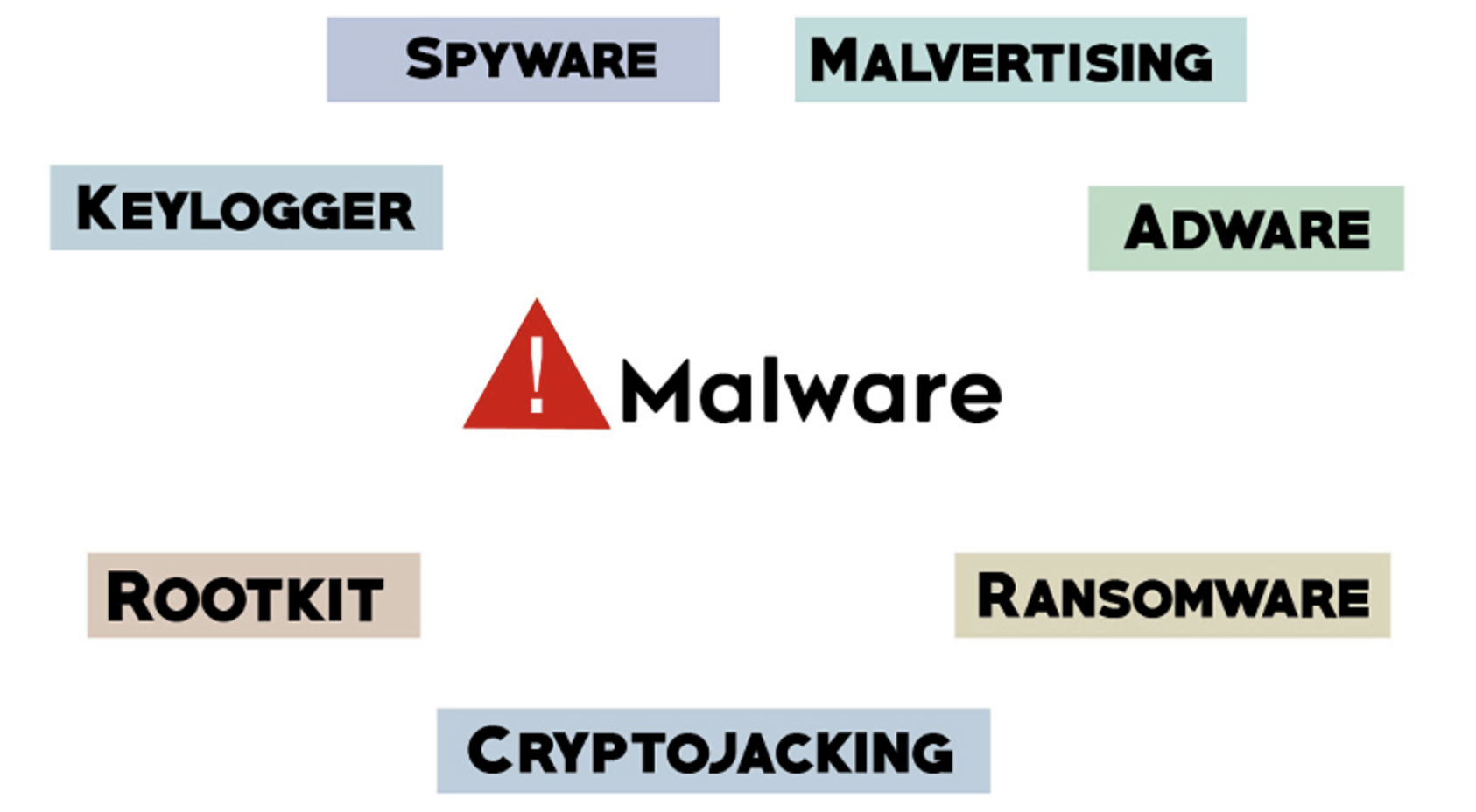
Malware typically refers to malicious software comprised of worms, viruses, Trojans, and several other harmful programs. Hackers and spammers use Malware to damage your data and gain access to your confidential and sensitive information. While no device is immune to malicious software or infections there are effective security practices you can implement to help prevent […]
1. Cyberattacks Affect All People Cyberattacks are so common in today’s world and recent reports show that hackers attack a computer in the US every 39 seconds! Once an attack happens millions of people could be harmed, businesses could be forced to shut down, and operations could be halted. Cyberattacks can happen on a global scale […]
Microsoft released Excel 4.0 for Windows 3.0 and 3.1 in 1992 and many companies still use this functionality in legacy operations. The issue is that bad actors have started using Excel sheets and macros as a new way to deliver malware. Tal Leibovich, head of threat research at Deep Instinct, which is a cybersecurity company specializing in endpoint […]
Security vulnerabilities in millions of Internet of Things (IoT) devices, including connected security cameras, smart baby monitors and other digital video recording equipment, could allow cyber attackers to compromise devices remotely, allowing them to watch and listen to live feeds, as well as compromise credentials to prepare the ground for further attacks. The vulnerabilities in IoT devices that use […]