No matter how big or small your business is, chances are there’s something cyber criminals can exploit. For these scammers, it’s not always about the money, any amount of data and information is valuable. Social engineering is the term used for a broad range of malicious activities accomplished through human interactions. It uses psychological manipulation to […]
Happy Cybersecurity Awareness Month! Throughout the month, we’re partnering with Sophos to provide bitesize cyber security guidance based on the event’s weekly themes. Week 4 Focus: Recognizing and Reporting Phishing Phishing emails fraudulently impersonate others with the goal of getting you to reveal personal information like passwords or card details. Be mindful, phishers commonly play on the following emotional triggers: Curiosity Hope Necessity […]
Microsoft Warns: Hackers are using open source software and bogus social media accounts to dupe software engineers and IT support staff with fake job offers, that in reality lead to malware attacks. According to threat analysts from Microsoft’s advanced persistent threat (APT) research group, a phishing hacking crew, linked to North Korea’s armed forces, has […]
Over 130 organizations, including Twilio, DoorDash, and Cloudflare, have been compromised by hackers as part of a months-long phishing campaign,security researchers call “0ktapus.” According to a report from cybersecurityGroup-IB, login credentials belonging to nearly 10,000 individuals were stolen by attackers who imitated the popular single sign-on service Okta. Attackers then used that access to pivot and attack […]
Our mobile devices are now the keys to our communication, finances, and social lives, making them lucrative targets for cybercriminals. Whether you use a Google Android or Apple iOS smartphone, threat actors are constantly evolving their tactics to break into them. This includes everything from basic spam and malicious links sent over social media to malware […]
Keeping on top of cybersecurity risks is a constant challenge. Threats including phishing, malware and ransomware are continually evolving and adapting, as cyber criminals regularly find new, innovative ways to conduct malicious hacking campaigns, break into computer systems and find a way to stay there. Many companies are having difficulties keeping up with the technological world and threats that come with […]
Cyber Security Awareness: What Are Phishing Attacks? Phishing attacks are the practice of malicious actors sending fraudulent communications that appear to come from a legitimate trusted source. At its core, phishing is an attack methodology that uses social engineering tactics to make a person take an action that is against their best interests. The goal […]
Our daily lives revolve around the internet more than ever, and with that comes risks. Cyberattacks have become an increasing issue and data breaches are the most common form of cyber crime. Experts estimate that there’s a new victim every two seconds. Despite this, data breaches aren’t hard to protect yourself from it just takes some […]
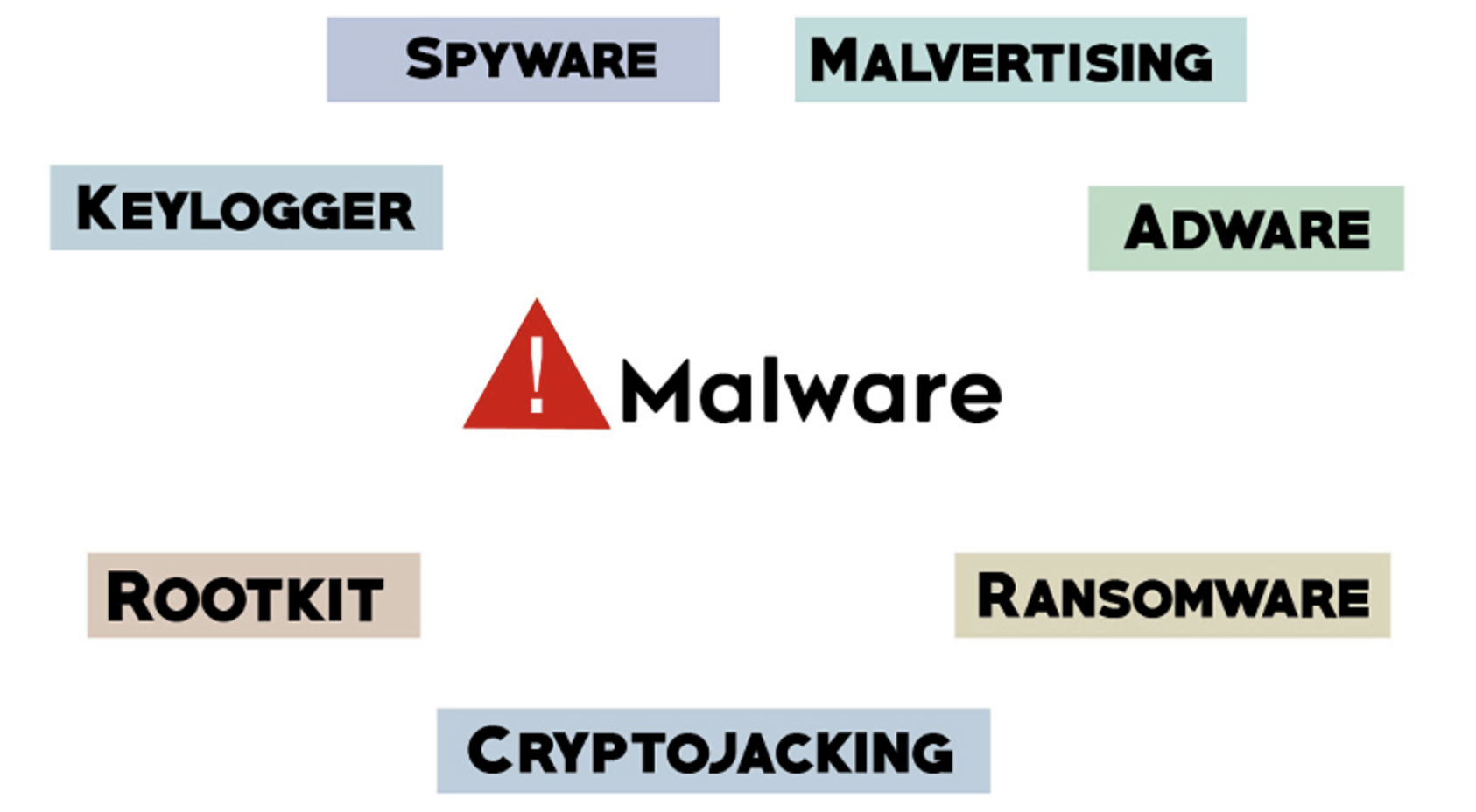
Malware typically refers to malicious software comprised of worms, viruses, Trojans, and several other harmful programs. Hackers and spammers use Malware to damage your data and gain access to your confidential and sensitive information. While no device is immune to malicious software or infections there are effective security practices you can implement to help prevent […]
- 1
- 2